Background
Typically, organizations utilize Zix Secure Messaging as a convenient alternative to Dropbox or other file sharing related tools because it’s easier to share sensitive information with users outside of the organization. Shadow IT has always been a standing issue among large enterprises and the ability to securely share files and communications with vendors, clients, and colleagues is a bridge that most organizations will eventually have to cross. Zix has addressed this issue by offering their secure messaging services, allowing organizations to integrate Zix with outlook. It’s a preferred solution because it gives Information Security teams oversight, preventing Shadow IT.
Identification
I received communications from a partner organization and had to register a “Zix Secure Messaging” account. When someone sends you a file or message and you don’t have a Zix account, you will get an email that prompts you to click on a button.

When a user clicks on the “Message” button it will take them to the organization’s home page for Zix Secure Messaging and they will have the ability to register an account to login and see what was sent to them. The email and Zix landing page can vary visually and from what i’ve gathered, Zix’s clients have the ability to upload their own logos and customize some of the forms and options.
The registration form seemed cut and dry.
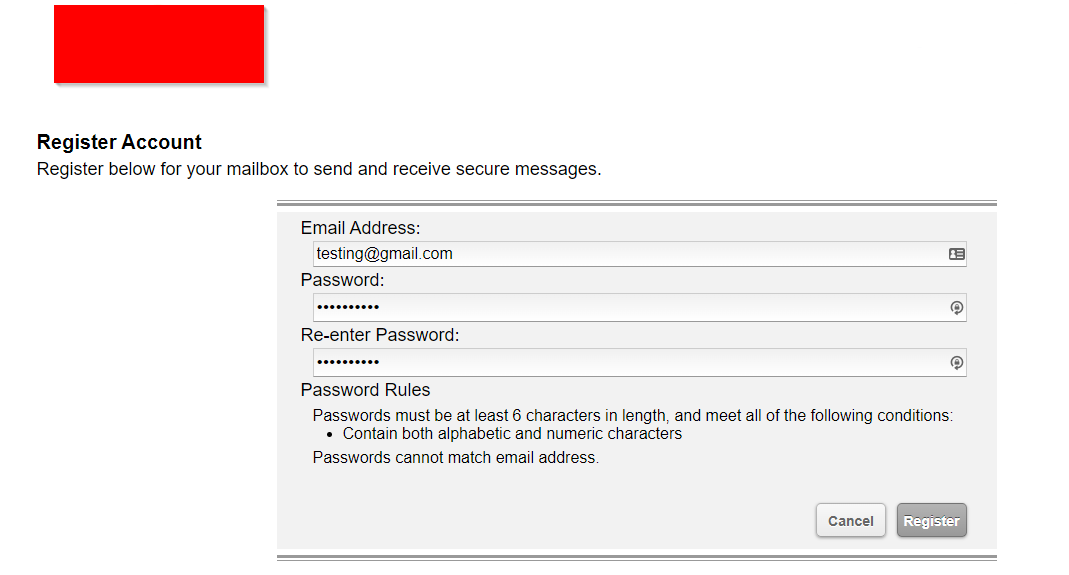
After clicking register, this form popped up:
Normally, I wouldn’t have thought much of this. It’s a standard registration form. In theory, many people can abuse registration forms, so it’s not that uncommon. However, my interest was peaked by a few observations:
- This appeared to be a standalone solution hosted by Zix.
- Employees have to register for accounts to see secure messages.
- There’s a good chance that employees have received or sent a secure message that would have to pass through Zix.
- Many organizations will setup accounts for employees on a whim, without telling them first.
Picking up what I’m putting down?
Exploitation
The only thing funnier than a good Cross-Site Request Forgery vulnerability is when a Business Logic Flaw helps you achieve a CSRF-like result [This isn’t a CSRF]. Do you hate the hassle of having to setup infrastructure or hope that your spear phish campaign doesn’t get burnt? Say no more!

Before attempting to attempt exploitation, I had to evaluate if this methodology was even sound to begin with. I registered with an email address that I own to check the legitimacy of the email.
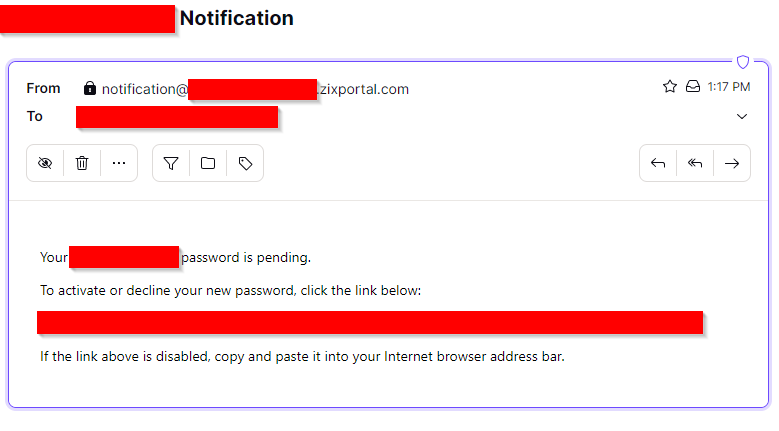
The wildest part about this email is that it appears to come from the organization. Oh wait, it does, because it IS from the organization. If a skeptical employee were to click on the link to see if it was legitimate, they would see the following:
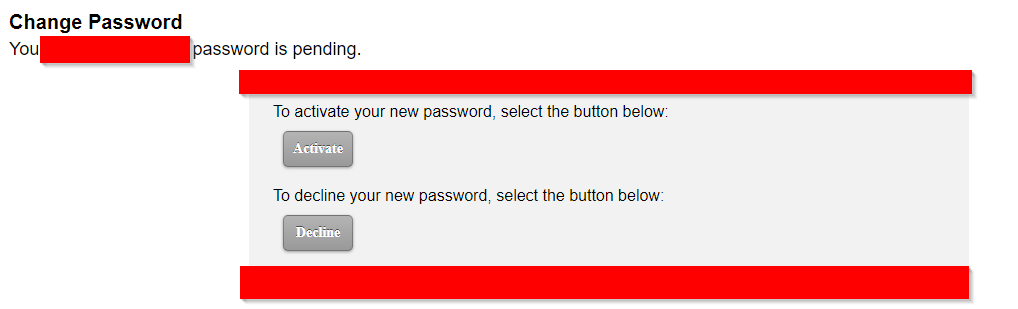
The domain would be hosted by Zix, with the organization’s name as a subdomain. It’s a legitimate domain, therefore it’s a lot easier to potentially trick employees. Social engineering is already an excellent vector and the propensity to initiate actions when the email comes from a trusted organizational source…well, you do the math.
Exploitation was simple. I clicked register and submitted various employee names enumerated off of Google with the following Google dork:
intext: "@company.com"
While registering these employees, I used the same password in-order to make it easier to check if the initial social engineering attempts were successful. In other words, don’t make your life difficult. Using different passwords would be OK, but you’re going to have to remember them. Scripting a login solution might be your best bet if you plan to go this route.
24 hours later, I checked multiple accounts, and some employees had fell for the attempts.
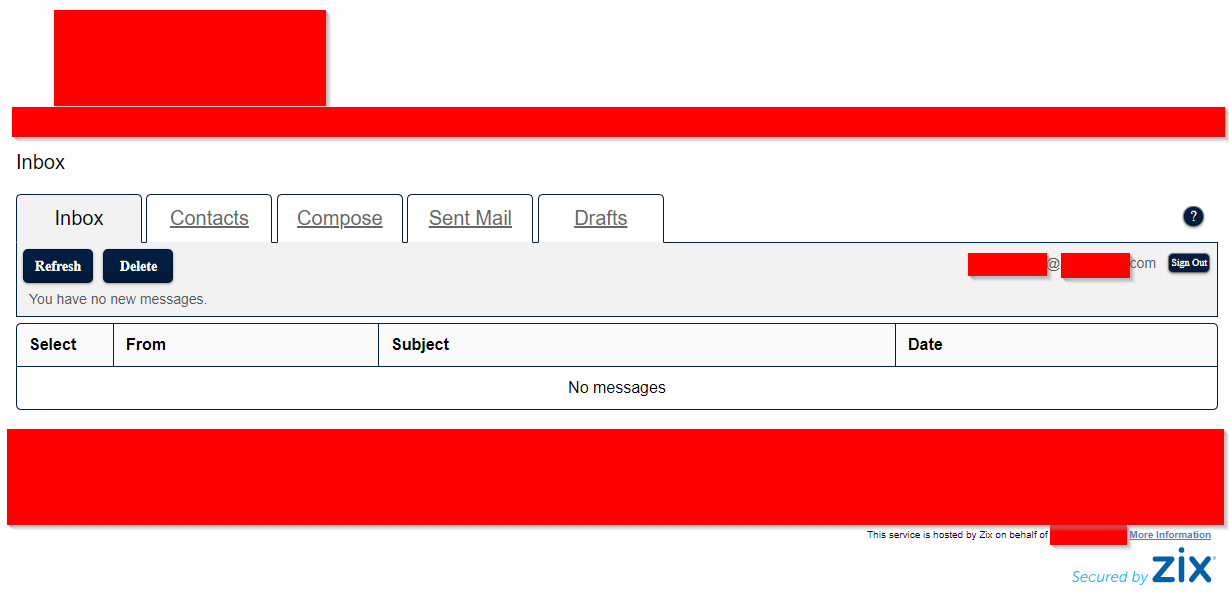
The best part about taking over an employee Zix account? It’s like having access to their primary work email. You can now perform spear phishing attacks as an employee of the organization with native attachments included <3
Here’s another example of yet another organization:
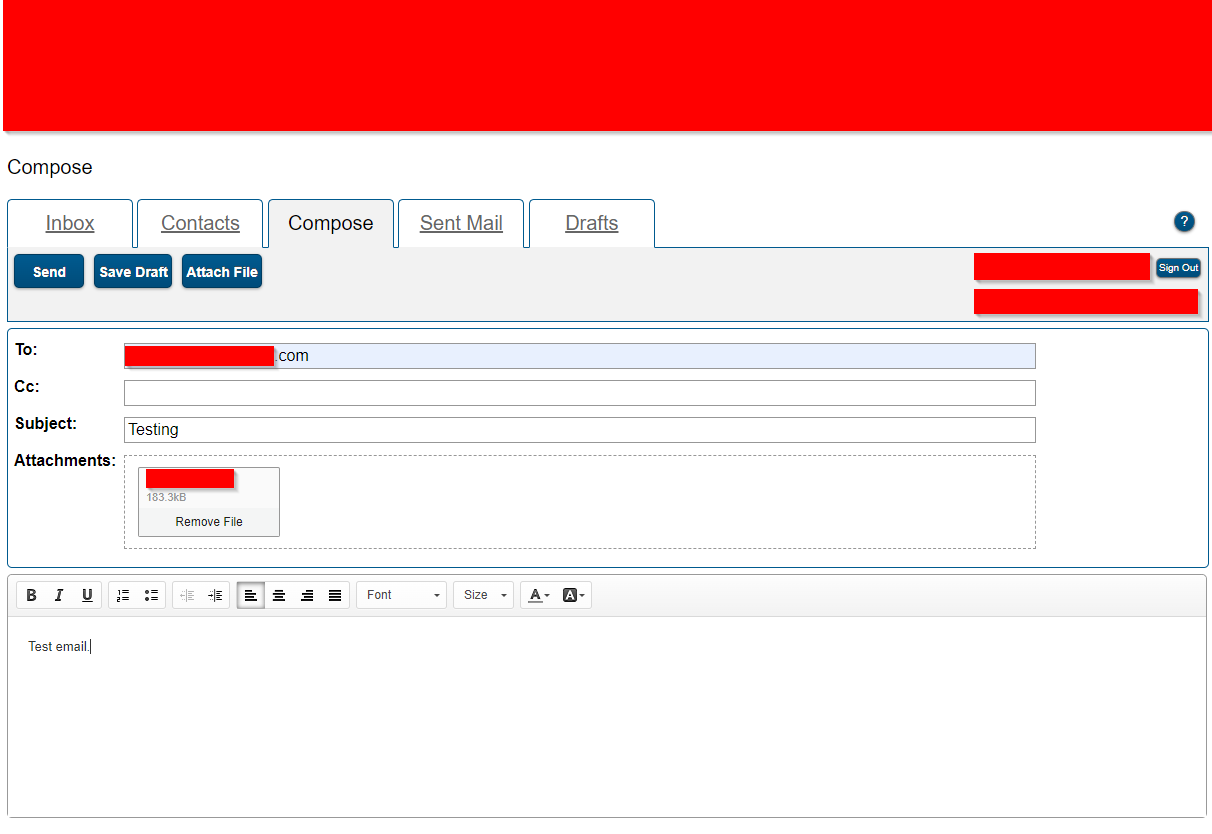
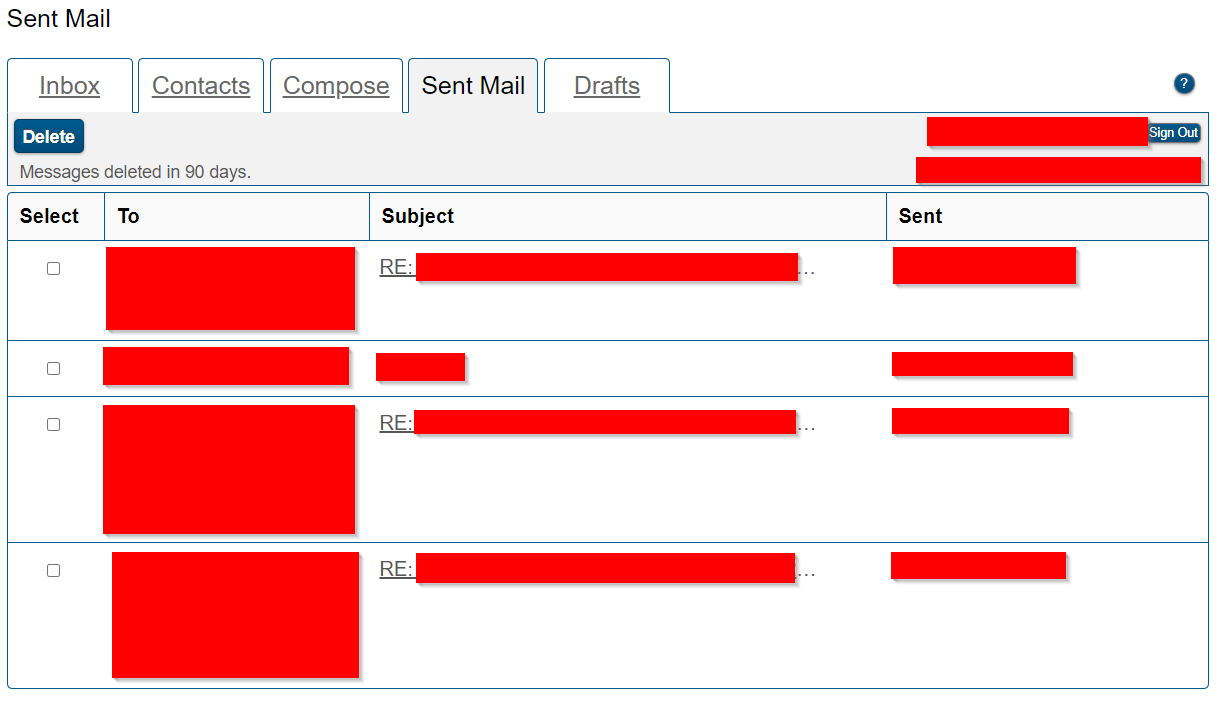
But wait! There’s more! In some cases, clicking on the “Sent Mail” tab can yield the attacker with some fantastic loot. It’s not unlikely to find employee rosters, bank account numbers, address lists, client contracts, sensitive archives, etc. Here’s an example of what the sent mail tab would look like if the employee has responded to sensitive emails in the past. If attachments are included within the email, you’ll see a paperclip.
Limitations & Workarounds
There are several caveats to this attack. If the organization is too small, you’re unlikely to yield successful results from this form of attack. In order for this attack to work properly, you probably want to target medium to large organizations where communication is difficult. It’s a lot harder to figure out what’s going on when your company operates in dozens of countries and hundreds of regions. The other part of this attack that increases the intensity is the sheer lack of operational understanding. You’re more likely to end up with one of your acquired accounts having its password reset than being prevented from carrying out further spear phishing campaigns.
Can this be prevented? Well, the answer is yes, but it requires the organization to rework the business logic of their Zix registration form - which also requires the organization to understand the general exploitation methodology. It wouldn’t be too difficult to see all of the account registration attempts and determine that someone was abusing the form.
Okay okay, that’s great - but how do I keep on spear phishin' with Zix?

You’ve heard it here first. Many of the organizations that were analyzed allow users to register, as you’ve seen. If you remember correctly - I stated that I first tested the registration flow with a personal email…wait what?? Yes, and while this may not be as effective as having an employee account, there’s still hope.
For example, if you’re trying to exploit an organization and you’re running into issues with employees falling for your account registration attempts, your next best bet is to squat a domain that looks like the target domain, customer, third-party partner, or use a standard automated message that might look legitimate.
Examples:
Target
galacticfederation.com
Ideas
SecurityOps@galacticfederateon.com
donotreply@galactiicfederation.com
galactic-infra-monitoring-alerts@outlook.com
The ideas are limitless. You might look at these email addresses and roll your eyes, but you probably know as well as I do that it works. A good email address combined with a 365 business account with a link to your malware might just do the trick.
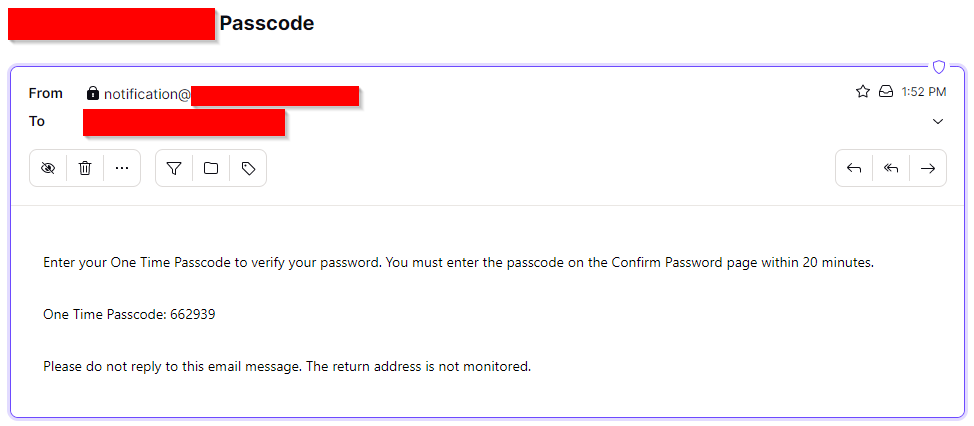
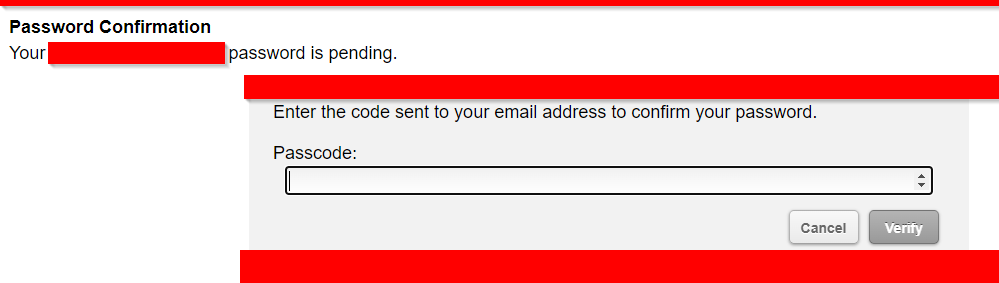
Enterprise prevention mechanisms in place are easily observable. Some of the organizations that I looked at wont allow you to register unless you have an email that belongs to the organization. In addition, the registration vulnerability is also severely hampered if the target implements the requirement to enter in a code after the registration flow is initiated. You can likely pretext an employee into giving you the code, but as any red team operator knows, this is going to make it more difficult.
Exploitability Assessment
Overall, I would rate the vulnerability impact as fairly high from a spear phishing perspective. When I conducted research to see if anyone else had discovered this vulnerability, I came across this news article:
https://www.armorblox.com/blog/blox-tales-zix-credential-phishing/
Abhishek Iyer writes, “we will look at a credential phishing attack that spoofs an encrypted message notification from Zix. Clicking the link attempts to download an HTML file onto the victim’s system.”
If you go a little bit further down in the article, you can see the statistics of this attack.
“This email attack was observed on multiple Armorblox customer environments across Office 365, Google Workspace, and Exchange. The total attack exposure was close to 75,000 mailboxes, but our threat research team found that small groups of cross-departmental employees were targeted in each customer environment.”
It seems that Zix Secure Messaging can be adequate spear phishing vector – however, one primary difference separates this observed attack from what I discovered…
The threat actors that have abused Zix in the past have used email spoofing to look like Zix. I observed the ability to take over employee emails, or when not possible, register an account of my own. This is astronomically worse because the success of your campaign doesn’t depend on infrastructure or setup. With this vulnerability, you get most of the bypass methodology, with the only social caveats being employees that are educated and report these attempts or detection patterns of one employee sending out too many similar emails. All in all though, those are standard campaign issues that both red teamers and APTs think about.
Be cautioned that the emails sent from Zix are still checked for malware. You still have to exercise bypass methodology for scanning/filtering if you’re going to upload files, but your best way around that will be abusing allowlisted solutions. This vulnerability gives a red teamer or threat actor a leg up because taking over employee accounts as a foothold to both gather sensitive organizational data and conduct more-trusted spear phishing is trivial.
This is currently unpatched. I don’t know if there’s a simple way for OpenText to provide clients with a quick way to change forms, or if clients will have to manually do it by hand. I tried to contact OpenText many times and got the runaround.
Timeline
Vulnerability Discovered | 6/1/2022
Attempt #1, OpenText Support Contacted | 6/2/2022
Attempt #2, OpenText Support Contacted | 6/8/2022
Attempt #3, OpenText Support Contacted | 6/17/2022
OpenText Support replies, Provides Different Contact Email | 6/24/2022
Attempt #4, New OpenText Support Email Contacted | 6/24/2022
Vulnerability Disclosed | 7/2/2022
Support
Need Red Teaming/Penetration Testing? Contact me and we can coordinate this through my company.
Looking for other services or want to contribute to my token project? Check out my services page!