United Nations Environment Programme Breached, 100K+ Employee Records Accessed
Executive Summary
We noticed that The United Nations had a Vulnerability Disclosure Program and a Hall of Fame, therefore Sakura Samurai 桜の侍 our security research group, set out to look for vulnerabilities to report to the United Nations. During the research process Jackson Henry @JacksonHHax , Nick Sahler, John @johnjhacking and Aubrey Cottle @Kirtaner identified an endpoint that exposed Git Credentials. The credentials gave us the ability to download the Git Repositories, identifying a ton of user credentials and PII. In total, we identified over 100K+ private employee records. We also discovered multiple exposed .git directories on UN owned web servers [ilo.org], the .git contents could then be exfiltrated with various tools such as “git-dumper”.
Exposed PII
Travel Records [Two Documents: 102,000+ Records]
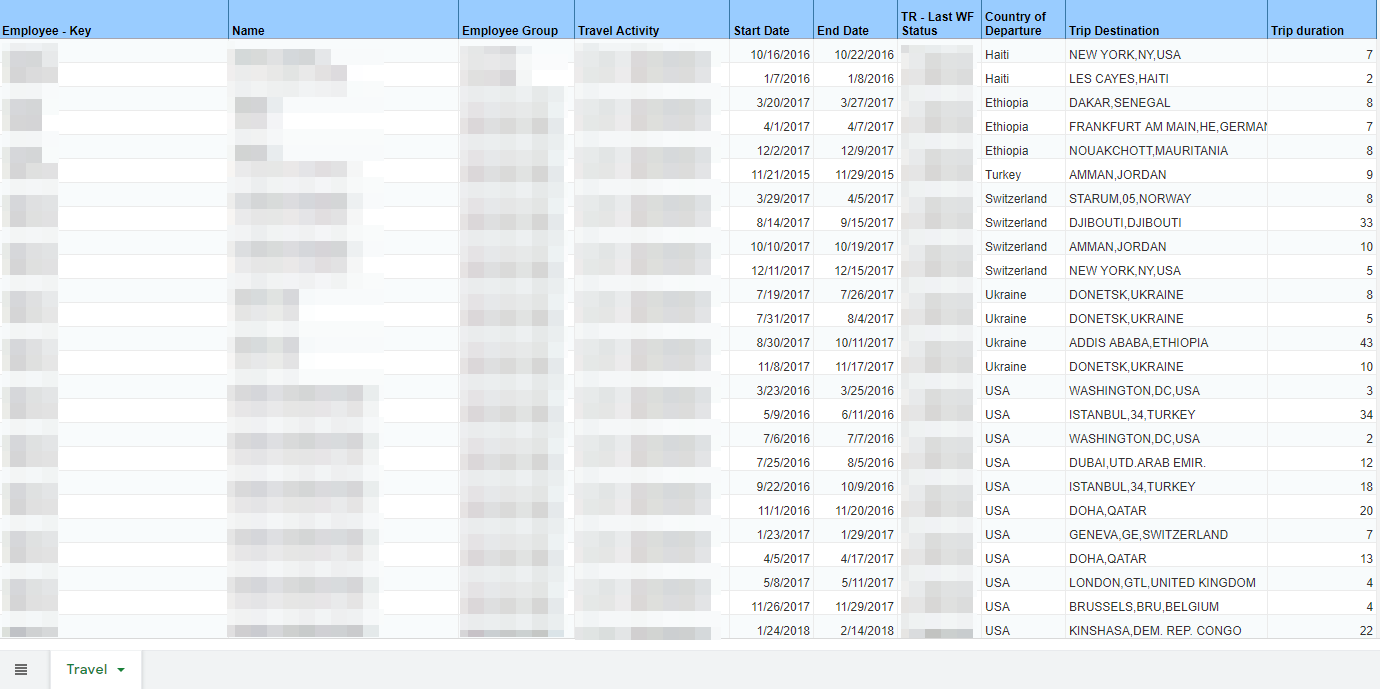
Travel Records Included Employee ID Numbers, Names, Employee Groups, Travel Justification, Start and End Dates, Length of Stay, Approval Status, Destination and the Length of the stay.
HR Nationality Demographics [Two Documents: 7,000+ Records]
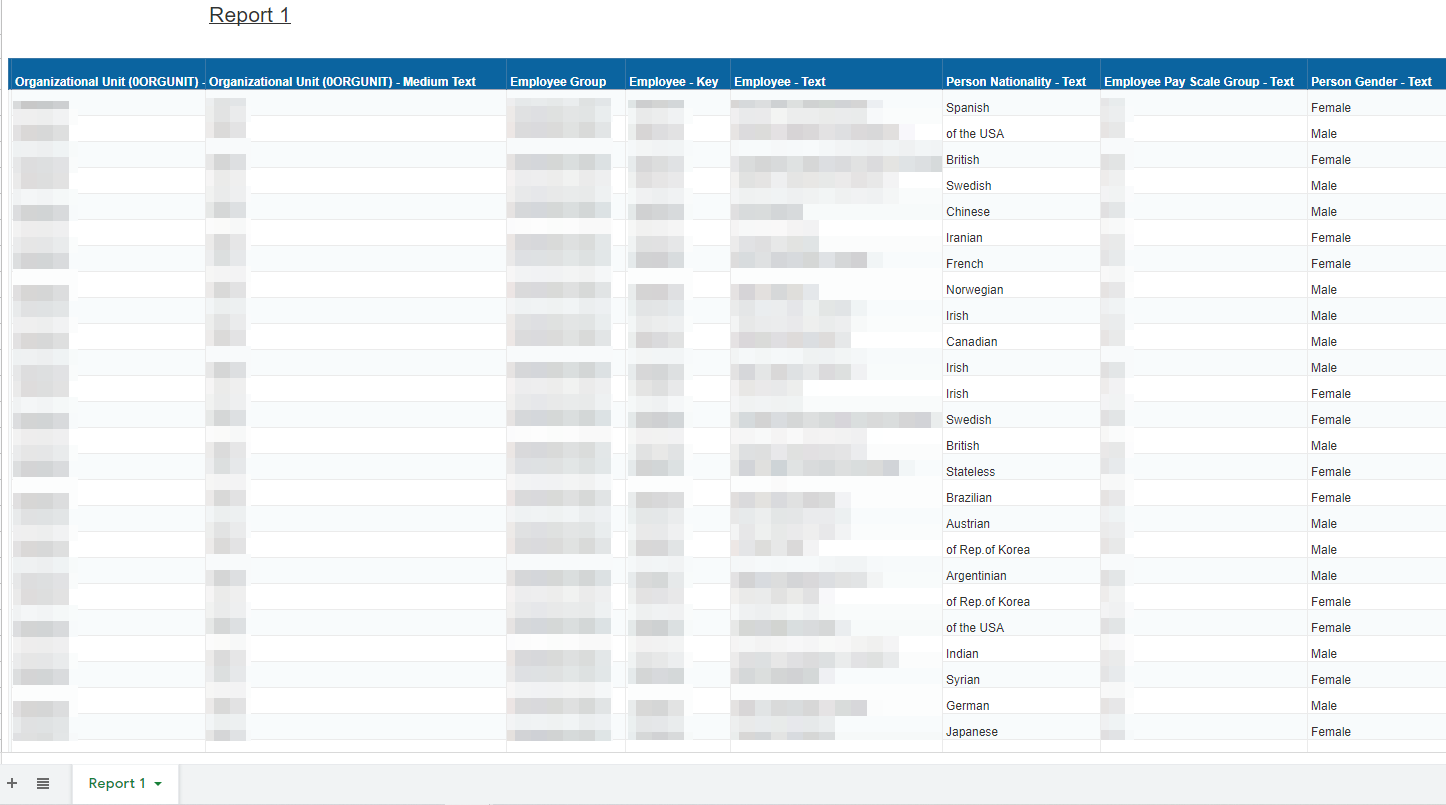
Included Employee Name, Employee Group, Employee ID Numbers, Person’s Nationality, Person’s Gender, Employee Pay Grade, Organization Work Unit Identification Number and Organization Unit Text Tags.
Generalized Employee Records [One document: 1,000+ Records]
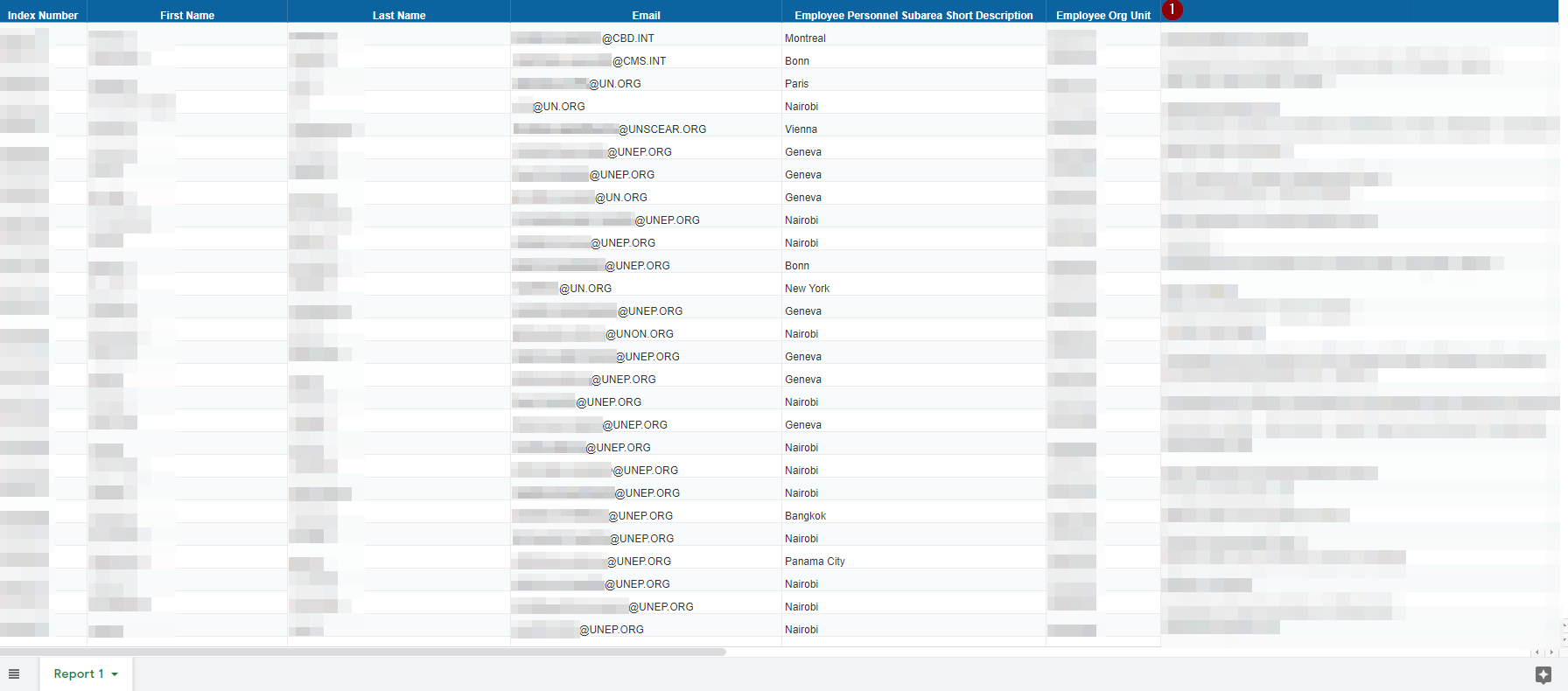
Index Numbers, Employee Names, Employee Emails, Employee Work Subareas and Employee Org Units. Note: The column with the “Red number 1” represent the Employee’s specific work department and was blurred as some of the sub-units are smaller.
Project and Funding Source Records [One Document: 4,000+ Records]
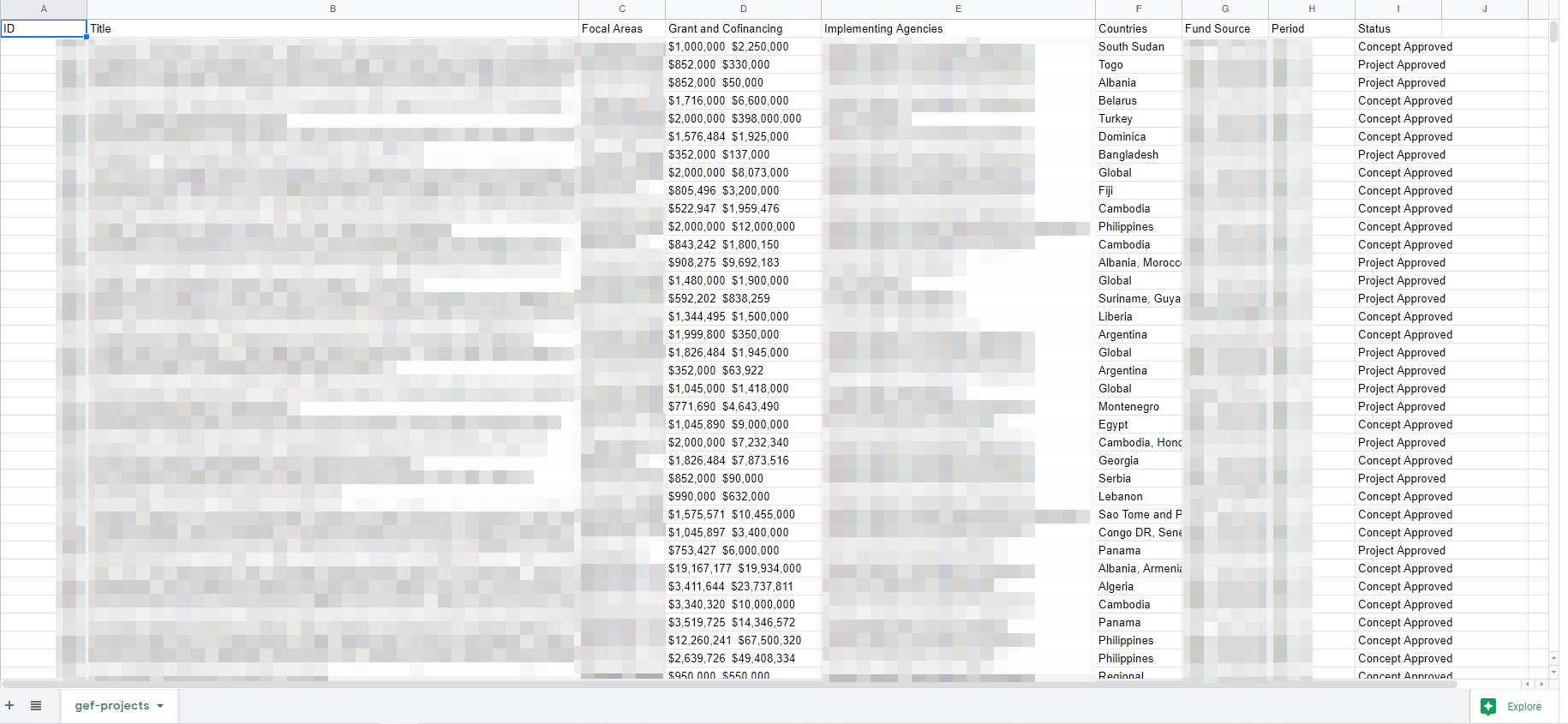
Included Project Identification Number, Affected Areas, Grant and Co-financing amounts, Implementing Agencies, Countries, Funding Sources, Period of the Project and if the Project/Concept was approved.
Evaluation Reports [One Document: 283 Projects]
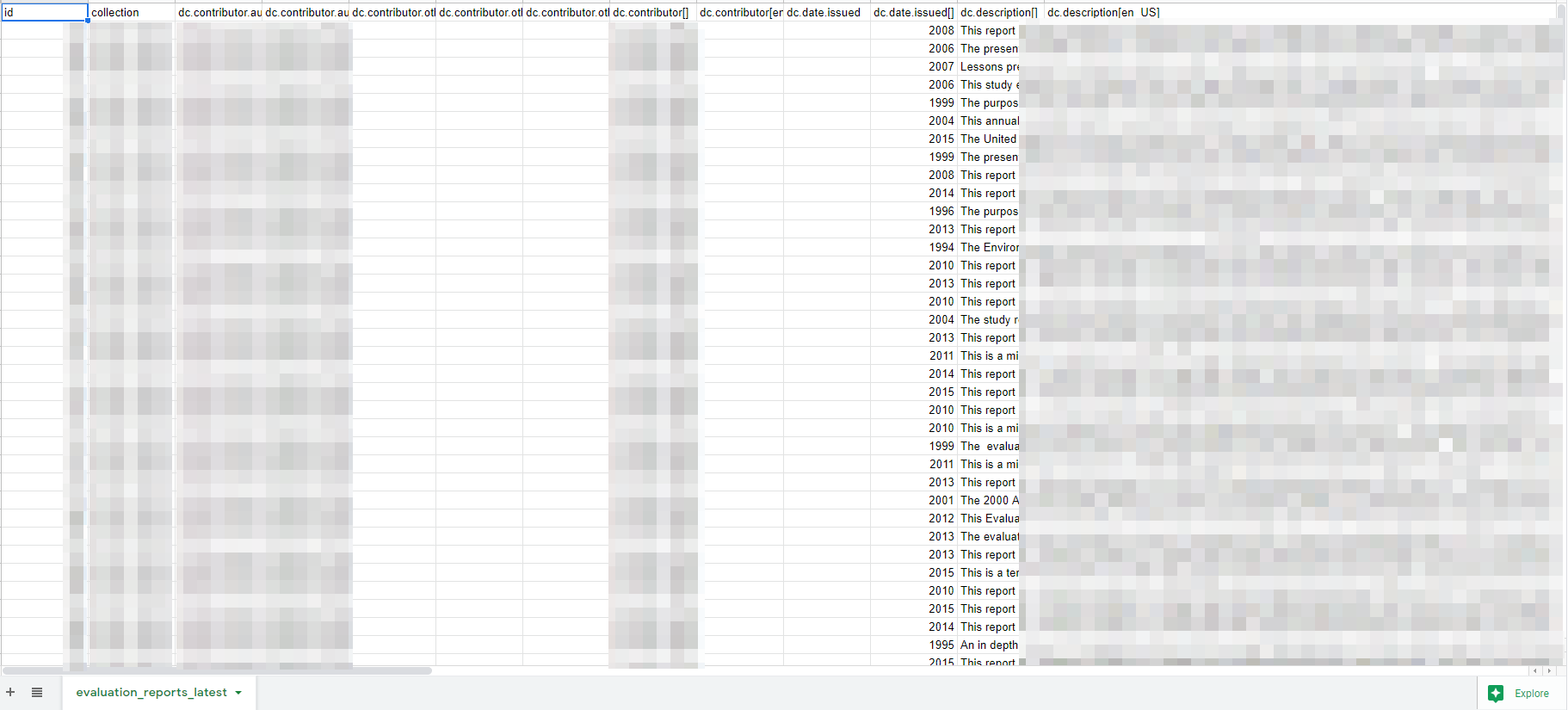
Overall descriptions of the Evaluations and Reports, Periods Conducted and a link to the report on the project.
Technical Assessment
In addition, on the lesser side of severity, we managed to takeover a SQL Database and a Survey Management Platform belonging to the International Labour Organization - also in the UN’s VDP program scope. However, it was of note that the ILO vulnerabilities were of little prominence as the Database and Survey Management platform were fairly abandoned in nature and contained hardly anything of use. Nonetheless, a Database takeover and admin account takeover on a platform are still Critical vulnerabilities.
We had performed subdomain enumeration of all of the domains in scope for the VDP offered by the UN. During our research, we began to fuzz multiple endpoints with tooling and initially discovered that an ilo.org subdomain had an exposed .git contents. Utilizing git-dumper [https://github.com/arthaud/git-dumper] we were able to dump the project folders hosted on the web application, resulting in the takeover of a MySQL database and of survey management platform due to exposed credentials within the code.
MySQL Credentials
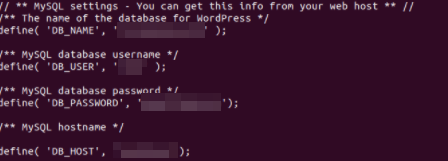
Note: We will not provide a picture of the survey platform due to the specific nature of the application.
After we had taken over one of the International Labour Organization’s MySQL Databases and performed account takeover on the survey management platform, we began to enumerate other domains/subdomains.
Eventually, we found a subdomain on the United Nations Environment Programme that allowed us to discover github credentials after a bit of fuzzing.

Ultimately, once we discovered the GitHub credentials, we were able to download a lot of private password-protected GitHub projects and within the projects we found multiple sets of database and application credentials for the UNEP production environment. In total, we found 7 additional credential-pairs which could have resulted in unauthorized access of multiple databases. We decided to stop and report this vulnerability once we were able to access PII that was exposed via Database backups that were in the private projects.
Check out our website
https://sakurasamurai.org
Twitter Links:
Main Page
https://twitter.com/SakuraSamuraii
Founders
https://github.com/johnjhacking
Members
https://twitter.com/nicksahler
https://twitter.com/JacksonHHax
https://twitter.com/Kirtaner
https://twitter.com/rej_ex
https://twitter.com/endingwithali