Summary
Many people do not know about the Jack Daniel’s Tennessee Squires. The Squire Association is an Elite Club for “friends of Jack Daniel’s”. Anyone that has ever dreamed of being a Tennessee Squire knows how difficult - if not impossible it is to obtain membership without paying thousands of dollars (or knowing someone who can nominate you).
Tonight, I give you an inside look of the Squire Association, and their practices. I found all of this information by first, taking advantage of a WordPress flaw, and then later, utilizing an Account Takeover Scenario as a result of a Business Logic Flaw. I was told explicitly that none of the information in my write-up is deemed private. In any case, there shouldn’t be any issues with disclosing a vulnerability that has been noted as irrelevant, posing no risk to user data, and it’s my duty to inform Tennessee Squires about an easy exploitation method that could result in unauthorized access to their account.
As a final note - I’m sad that this post will probably result in my Tennessee Squire Nomination being pulled, but I’m a firm believer in educating users on the result of inadvertently exposing their information, and educating the business in the importance of identifying and squashing Business Logic Flaws (or at least fulfilling a patch when the researcher reports the flaw for free - especially when there are various exploitation scenarios attached)
Initial Findings
Nearly a month ago, I found a simple vulnerability against the Squire Association’s website. Unauthenticated WordPress REST API access allowed me to see many of the internal posts within the website, unrestricted - as well as the simple disclosure information such as username, etc. While the WordPress vulnerability is hardly considered critical, the ability to see internal posts allowed me to intercept private Squire invitations.
Initially, I had trouble registering because I did not have a key piece of information involved in the registration, the “Squire Plot Number”. A quick Google Search brought up hundreds, if not thousands of plot numbers, so bypassing this restriction was fairly simple. It took 5 minutes to end up with an invitation on my calendar.

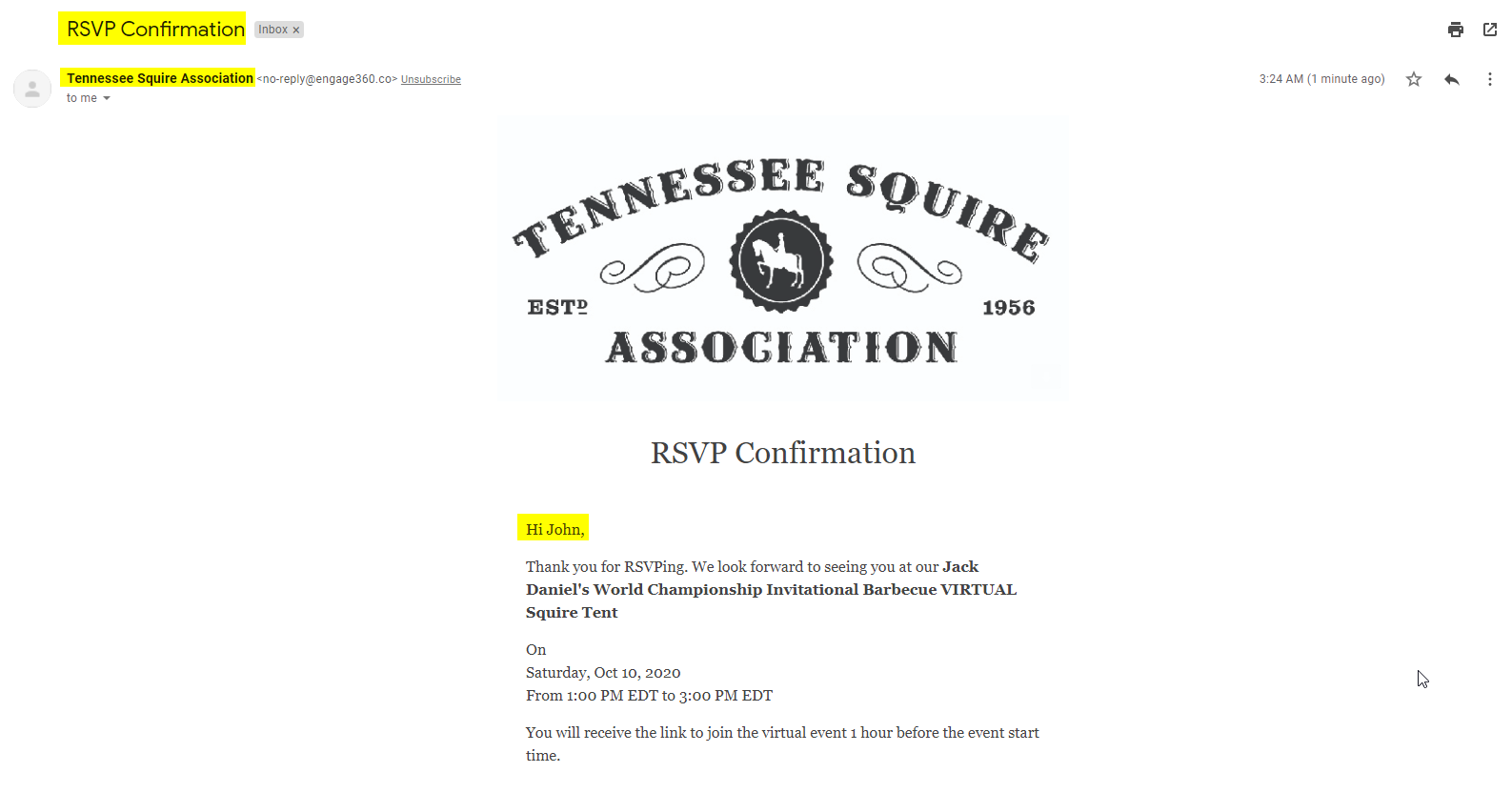
As stated, I was also able to see internal posts:
I went through the process of a quick and dirty lookup of a lot of the post-information that I had found, but did not come across any of it through public sources.
Reporting
The reporting process was difficult. I tried multiple means of contact, but once I was able to get in-contact with the right person, triage of the vulnerability was smooth. The employee appreciated my thorough report, and ultimately - I was satisfied with the outcome. They quickly remediated the REST API vulnerability, and I validated. In addition to the vulnerability fix, the employee had this to say:
First of all, I want to thank you for the thorough report. Our IT team went through and quickly made updates to cover off on the issues that were most concerning. The ability to view the content without logging in and registering for the event weren't major issues because that information makes its way out into the non-Squire world once we share with Squires. They just usually are the first to know and the first to share with their friends. But regardless, I appreciate your persistence and helping us uncover these issues. We certainly take them seriously.
A couple things, you mentioned wanting to be a Tennessee Squire and without a doubt, an act like yours is exactly what we are looking for in our Tennessee Squires (along with a love for Jack Daniel's, of course). I would love to nominate you and also send you a package as a kind thank you from your friends at Jack. If you wouldn't mind sharing your address, I'll get the nomination submitted and approved, then get a package in the mail for you.
Also, as I mentioned before, we take these issues quite seriously when it comes to any consumer data and our systems. We will review the login procedure and get that corrected going forward. If you wouldn't mind exercising discretion, it would be greatly appreciated. Thank you again!
I agreed to the resolution because at this point in time a Threat Actor would have to:
1. Want to know a lot of non-sensitive information about the Squires.
2. Care enough to intercept invites that could be acquired through the OSINT process.
Nonetheless, I thoroughly appreciated the response, and I had hoped that they may rework the logic behind authenticating to events with a plot number that can easily be found. We parted ways in our discussions.
Inadvertently Brainstorming New Exploitation
Obviously, at this point I had discontinued conversations about any additional website logic. It was clear that the exploits defined above were not “ground-breaking”. Surely they value their user experience, however, being able to find out private information about the organization and attend events were all within the scope of OSINT, should a person care enough to dig.
Yesterday, I had a look at my report because I was curious about the logic behind authenticating for the events with the Squire Plot Number. To my surprise, I found something that I had previously overlooked - the login page for https://www.tennesseesquires.com/ only requires the Email Address and the Plot Number. I remember why I had overlooked this piece of information. In my head, with no second thought, I believed that there was no possible way JD was using a plot number as a password. I had assumed that it was just a part of the login flow, to get to the password field:
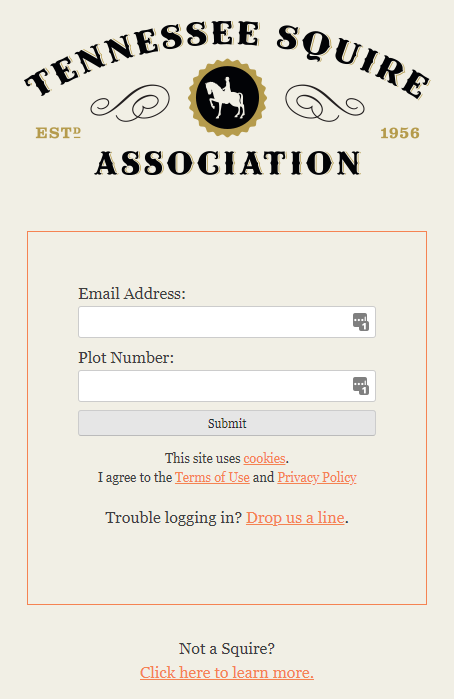
Turns out, I was dead wrong. My heart started racing. Knowing how many plot numbers were exposed, and how easy it easy to obtain a person’s email, I got to work. It didn’t take long to stumble upon this beautiful gem:

Basically, this is an invitation letter (along with a land deed that is provided to the Squire).
I went ahead and redacted all of the information for the person, even though they were not smart enough to do so [which is a little scary because it has their address, email, and plot number]. This part of the equation is not necessarily Jack Daniel’s fault by any means - a person must be weary in regards to posting their private information online (Especially if it’s their account login LOL) At least I didn’t have their plot number, right?

Opps. Looks like the classic result of Human Error. The Human Element. The newly-crowned Squire is overflowing with excitement, and rushes straight to Twitter/Instagram to post all about it. Between these two photos we now have their Home Address, Plot Number, Personal Email and Full Name.
I still didn’t know if this was a joke or not, I believed that there might be a password that would be setup upon first login. Surely a login attempt wouldn’t work…..right?
Spoiler Alert: The login attempt didn’t work.
Friend: Dude! Guess What?! I just became a Tennessee Squire!
Me: No way, really? Let me see!
Looks at document
Me: Sick bro! What’s your email? I want to send you something cool.
Friend: fake@example.com
Me: Okay cool. I’ve taken over your Squire Account.
Friend:

The login not working didn’t stop me. Within minutes I had 50+ Full Names tied to Squire Plot Numbers, and that was just on the first couple of pages of Instagram, using the tag #tennesseesquire
I noticed that Twitter also had pictures that Squires were posting of their invitations. At least some of them were smart enough to redact their plot numbers.
I attempted another login with another enumerated email and plot number:

Well, honestly - I didn’t expect a login event by using an email/plot number to work. Surely Jack Daniel’s must know that people consistently expose their plot numbers online.
Anyhow, the employee that I triaged the earlier vulnerabilities with told me that there wasn’t any private information that can’t be seen by the public, so I’ve compiled a cool-little archive of info!
Archive of the Tennessee Squire Association Information
https://github.com/johnjhacking/TennesseeSquires
Again, none of the information is Private (as the employee has affirmed) therefore, enjoy some cool reading about the Organization!
Reporting
I went through a near-identical reporting process with this vulnerability, however, this time I had a direct line to the employee. I reached out via email and received no response. Being that their phone number was attached in their email signature, I reached out.
I let them know that I would likely disclose the vulnerability, and that it should be fixed, their response was:
"There isn't any account information on the other side of the login, so essentially they are logging into a static site. Not a site where they can manipulate account info. And as I said before, none of it is private."
Their response was clear. There would be no harm in disclosing any of the internal information. None of it is private! It’s apparently impossible to manipulate account info (because I can’t Social Engineer the company into updating my information) - Clearly they haven’t seen Rachel Tobac’s work.
Impact
The risk was accepted, and the vulnerability will go unpatched. Here are several reasons why I believe that this instance of account takeover could possibly result in further exploitation:
Disclaimer, I obviously didn’t attempt many of these exploitation methodologies, therefore I cannot vet the authenticity or probability of it working - however, it’s my best working theory of the methodology
-
Threat Actors Can Sell Acquired Accounts:
It’s not a surprise that being a Tennessee Squire is a renowned honor. Many have attempted to become one, but have come out empty-handed. With that being said, it’s not improbable that Criminals will use this to their advantage to sell account access. In fact, there’s no functionality to change the password. The Squire must use their plot number as the password, so one account can be sold over and over again.
-
Nominate Other Members
As you may have seen in the Archive, Squires have the ability to nominate three other squires per year. Realistically, not every nomination is successful, but what’s to stop a Threat Actor to attempt a nomination on behalf of a Stolen Account? In fact, I have seen more than a dozen websites/posts that claim they can nominate and get you membership for a price. Feel free to do your own research. I cannot vet the authenticity of the claims nor do I associate myself with the immorality that comes from scalping a Squire membership.
-
First-Look Access to Events/Releases
The employee claimed that this isn’t private because Squires will share events with their friends and family. I can concur with this point, but, it certainly makes the process easier for someone who doesn’t know a Squire.
-
Nomination Pool Disruption
Being that a member can submit a nomination, my theory lies in the school of thought of being able to Script the disruption of the Nomination pool with fake-information. Depending on the Web Application setup, this could result in having to wipe the database and implement rate limiting controls and filter the information. What would happen in the event that the Squire Association had to review 1M+ Applications? Since I haven’t tested this feature (because I didn’t want to abuse the system) I don’t particularly know if they are implementing a rate-limiting feature, so at worst, a Threat Actor can taint the entire database using multiple-user accounts (or maybe even one), and at best, the Threat Actor can burn up all of the Squire’s nominations and the Squire will not realize it until they go to nominate someone.
-
Intercepting Gifts
Someone who wants to be a Squire would want to utilize full functionality of the Squire Association. The ability to update User Information is depreciated, however, as we all know, Social Engineering is easy. What will stop a threat actor from emailing the provided account-update email distro and Social Engineering the team into believing that they are the account owner? The scenario isn’t unrealistic, and many of Jack Daniel’s gifts have resold for 200+ dollars as they cannot be acquired anywhere else.
-
Business Reputation Impact
I’m not going to argue this point. It’s too theoretical. However, I will ask you this: Do you want to share your account with some random stranger that has successfully managed to login to it?