OSCP Reborn - 2023 Exam Preparation Guide
Prologue
Many of you are likely aware that the Offensive Security Certified Professional Exam was revised, with the changes officially published on January 11, 2022. The old version of the exam required the student to perform a buffer overflow attack (it still may end up on your exam, but is not a guarantee). Since then, the model has shifted towards an active directory model which is more aligned with modern day penetration testing.
The original plan was to completely sunset the OSCP preparation guides. LaGarian Smith who passed the OSCP in April of 2022, volunteered to review and cross check my active directory resources against the modern exam, and add his own methodology. Thus, OSCP Reborn came to fruition.
It’s important to note that the predecessor to this guide, was segmented into several sections to explain various aspects of penetration testing to all skill levels. Rather than revise the old guide, there will be a brief section in this guide that redirects new hackers to basic resources if they are learning and not specifically ready for OSCP preparation. While the guide briefly covers resources for beginner hackers - it’s not primary goal of this resource. I’ve just learned from previous guides that beginners almost always stumble upon the OSCP guide, and don’t know where to start overall.
Feel free to skip to the “Pre-PWK” section if you’re ready to start preparing for the OSCP.
For Beginners
If you’re new to hacking, you should start by learning the basics of networking and security. If you don’t, you’ll have a difficult time understanding hacking.
- Network+ - Professor Messer
- Security+ - Professor Messer
- Pre-Security Path - TryHackMe
Subsequently, the following resources can be utilized after a baseline level of technical knowledge is established, in this order:
- Jr Penetration Tester Path - TryHackMe
- Practical Ethical Hacking - TCM Academy [Includes AD modules]
It’s not a requirement, and I can’t personally vouch for it, however I’ve heard that the eJPT certification is a great beginner hacking certification. I would recommend getting this certification done as a way to learn more hacking and test your knowledge prior to moving on to more advanced resources. If you can’t pass it, you should probably go back to TryHackMe and practice on the many boxes and other resources available for explaining hacking concepts.
- Junior Penetration Tester - eLearnSecurity
Pre-PWK Preparation
New hackers should strive to ingest as many resources as possible and hack a wide array of machines before starting the PWK. While it’s true that the PWK is the “starting” point prior to the OSCP examination, the last thing that you want to do is waste precious PWK lab time by getting familiar with concepts that you should already know. The PWK course should be a mild supplement to your existing knowledge, if done correctly.
Meet the following prerequisites:
- Basic understanding of networking and security
- eJPT certification or previous experience rooting both Windows and Linux systems
- Basic knowledge of Exploit-DB, Github exploits, and modifying/fixing exploits to work against the victim system
- Moderate understanding of network and web application services
- Basic experience conducting reconnaissance and identifying vulnerabilities
- Writing exploits for buffer overflow vulnerabilities
If you’re at this point, you have probably already found your way into an entire slew of resources. TryHackMe, HackTheBox, Pentest Academy, PentesterLab, Proving grounds, etc.
Since the OSCP now includes an active directory section, one of the best ways to prepare is by specifically tailoring your operations to account for course revisions. Fortunately, there are already resources available at a low-cost to get familiar with active directory.
Active directory preparation modules
- Compromising Active Directory - TryHackMe
Hands-on active directory hacking preparation
- Throwback - TryHackMe
- Wreath - TryHackMe
- Holo - TryHackMe
- TCM Academy [AD sections 15 through 19]
Understanding the basics of active directory exploitation will save you a lot of time when reviewing the PWK material. Active directory is a large portion of the examination, and has a lot of components and hacking methodology associated with it.
In addition, getting familiar with these active directory resources can make a difference. Please ensure that you are not using automated exploitation tools that are expressly forbidden on the OSCP examination. Offensive Security usually never maintains a comprehensive list, so a good rule of thumb is: if it’ll do all of the work for you, it’s not allowed. Heed our warning, and utilize various resources but still, do not be afraid to use custom enumeration tooling from Github that doesn’t violate the defined parameters of the exam
The ultimate repository of AD hacking
- Active Directory Attacks - swisskyrepo
Once you’ve reviewed the following resources, and practiced the defined above, it is time to move into the PWK.
PWK
Before any methodology is mentioned for completing the PWK, Offensive Security offers (10) bonus points to students with two options. Click the link here to learn more about the bonus points as they MAY come in handy for the exam.
Starting the massive PDF that OffSec provides can be daunting. Without a constant schedule, completing all of the exercises will be a challenge. It is suggested for beginners to complete all of the exercises, but since you already did the pre-work, personally, we recommend skipping the exercises and starting in the lab to gain more experience. If you decide not to pursue bonus points, there’s less buffer room – so be warned.
The Lab
Proving Grounds and the lab environment are different because in proving grounds, the machines are rated. Instead they start you off with a Learning Path of about 11 machines to begin your lab. The machines do vary in range of difficulty, but pwning some of these boxes unlock different subnets within the lab. TAKE NOTES AS YOU WORK THROUGH THE BOXES!! To simplify, if you don’t – you might end up missing key artifacts that give you clues to the exploitation of other systems.
Speaking of notes, while moving through the PWK, one should be adding to the repertoire of notes gained from the Pre-PWK learning material. While everyone has a preference, building a cheat sheet based on the ports and vulnerabilities found/exploited will speed up enumeration while scanning the lab machines in the course. There are many useful cheat sheets that could be a great starting point; example: Cheat Sheet, but be warned that creating your own cheat sheet and working from it proved to be valuable because referencing your own cheat sheets becomes second nature, contrary to using others.
PWK Active Directory The PWK lab has three sets of AD deployments that you must complete to be prepared. Everything you need to pass the AD portion of the exam is within the lab. The first set recommended is Sandbox Assembling the Pieces. This portion is great as it walks through the exploit process in gaining a foothold into the domain (the hardest portion for the exam). Using SQLi, password cracking, RCE, post exploitation based enumeration, and many other tedious tasks needed to pwn the domain are involved.
Since there will be two more sets of AD deployments, it’s recommended to save (1) set for a 24 hour pre-exam conditioning dry-run while lab access is still available. Saving a set will be the new method of pre-examination preparedness, as opposed to doing a HackTheBox dry-run (old method). Below is a recommended set to test for preparedness:
PWK (w/ AD): 10.11.1.120-123, 10.1.1.68, 10.1.1.89, 10.1.1.95, 10.1.1.98
The above has no buffer overflow boxes included as conducting an overflow is the least of your concern. Ensure that you operate with realism in mind, taking notes and typing up a mock report even if you know you did the AD boxes listed (no peeking). Doing so will test your technical skills, time management and note taking abilities – all crucial parts required to pass the OSCP examination.
The OSCP Exam
Get some rest, eat well, and be sure to take breaks. The gist of the general tips that you’ll receive from people have taken the OSCP all cover these key points. Let’s focus on the critical parts of the examination.
Note: LaGarian has informed me that getting a Buffer Overflow on the exam is still a possibility. While lower priority, ensure that you practice overflows, as you can’t assume that you will not have to touch one on the examination.
Points
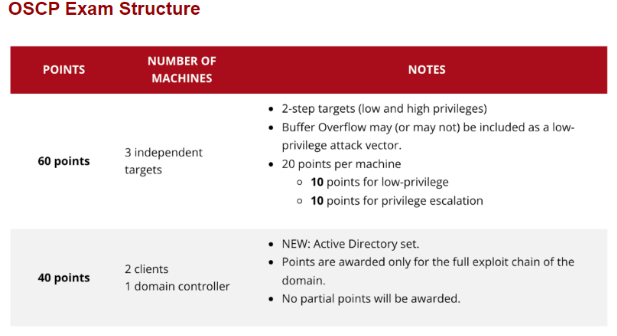
Generally, most people who have done enough research understand that 70 points is considered a passing examination score. Several different strategies are available, and we will analyze what makes sense based on bonus points from the labs versus no bonus points. Remember that you should never fully depend on the 70 point technique and you should continue to do everything in your power to acquire as many points as possible. Fully in the context of this guide represents getting the local.txt and proof.txt files.
With 10 Bonus Points
- Fully exploit all 3 non-active directory targets for a total of 60 points + 10 bonus points
- Fully exploit 1 non-active directory target – 20 points + Full exploitation of active directory targets – 40 points + 10 bonus points
- User level access on 2 non-active directory targets – 20 points + Full exploitation of active directory – 40 points + 10 bonus points
Without 10 bonus points
- Fully exploit 1 non-active directory target – 20 points + User level access on 1 non-active directory target – 10 points + Full exploitation of active directory – 40 points
- User level access on 3 non-active directory targets – 30 points + Full exploitation of active directory – 40 points
As you can see, there’s several examples of strategies that can set you up for a baseline level of preliminary success. The most important concept to understand is that you will not be awarded partial points for anything in Active Directory. To simplify, this means that if you did not achieve the lab bonus points, you need to immediately move on to the active directory portion of the exam after fully exploiting 1 non-active directory target, and gaining user level access to another non-active directory target. If you achieved the lab bonus points, the best strategy would be fully exploiting one non-active directory box, then focusing on full exploitation of the active directory.
It is not recommended to immediately attempt to pass the examination through full exploitation of all 3 non-active directory targets rather than a mixture because the likelihood of running into technology that you haven’t exploited before is fairly high. The active directory portion will be your bread and butter, and the techniques utilized are fairly consistent.
Taking notes
The concept is simple: take efficient notes or bust. No one wants to have to go through the exploitation methodology again, just to take a couple of screenshots. After every major event, you should strive to take simple notes that reference key pieces of information.
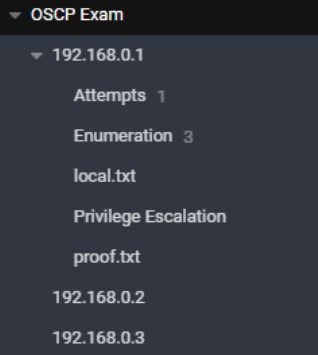
Joplin was utilized as my preferred note taking tool. Cherrytree, Obsidian, or Trilium work all the same. The key principle to remember is that you should segment every machine by IP address, and categorize each parent note into corresponding sections such as enumeration, exploitation, privilege escalation, proofs, etc. In addition, I like to have an “attempts” section of my notes that focuses solely on exploitation methodology that did not work. Not repeating the same methodology that has proven not to work is crucial and will save you time. It will also keep you organized to easily run through techniques that you haven’t utilized. Another section you can have is an “interesting” section that focuses solely on documenting possible attack vectors to try.
After gaining an initial foothold, take notes on how you did it with extensive screenshots. Rinse and repeat when performing privilege escalation. You need to be able to explain every step of the process in depth. Take notes now, save time later.
In each section, don’t be afraid to dump random pieces of information. I like to dump all of my scans directly into their own sections for easy reference.
Enumeration methodology
Immediately begin running nmapAutomator or your preferred recon tool on each target, in parallel. As interesting results popup, go through the methodology of attempting to enumerate manually or with other tools. The reason you’re being told to do this is because you do not want to have to wait for all of your enumeration results to come back - it will burn your exam time. If you enumerate everything at once while picking one target to look at, you’ll have plenty of recon to look at with nmapAutomator once you burn out and want to switch to another target.
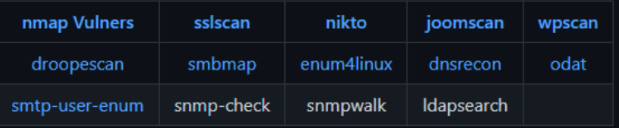
As interesting ports and services reveal themselves, you should start utilizing other tools tailored specifically to that service. For instance, using dirsearch for fuzzing web applications could net you more results than something like Nikto or ffuf, etc. The point is, using multiple tools per service will give you a greater depth of reconnaissance.
When it comes to enumeration methodology on specific ports or services, ensuring you go through the proper motions will be key, so methodology found on HackTricks can be the way to go when you need quick command cheat sheets for various ports and services.
Other enumeration methods that aren’t discussed often are manual business logic methods. For example, can you register an account on a web application that has a signup? Does the account have the ability to upload .aspx, .jsp, .war files and access them? Business logic requires the hacker to think outside of the box to utilize legitimate functions to abuse them in unintended ways. Offensive Security isn’t beyond this, they may very well throw you a curveball. These types of issues fall into enumeration because they are a precursor to developing exploitation techniques.
Arguably, one of the most important processes is thoroughly documenting the software and services used on each port. Quickly doing this will make it easier for you to understand related exploits.
Obviously we cannot cover every single tool or enumeration methodology, but with the resources described you’ll be in a far better position.
Searching for exploits
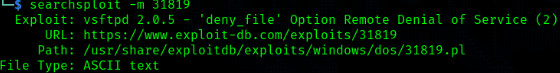
The process of finding exploits that work against services has never been easier. Using searchsploit, you can check for known exploits against various software that you may discover. Also, pro tip: searchploit -m will pull the exploit for you ;)
The least talked about way of identifying working exploits is by searching through Github. Let me show you something that will change your life.
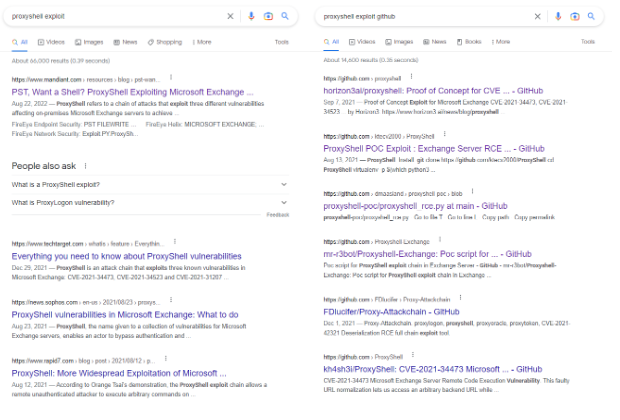
Two photos, simple difference. “Proxyshell exploit” will net you astronomically different results than “proxyshell exploit github”. Practice your google skills, which is essential to find relevant exploits to use on the OSCP exam. The search on the left pulls up mostly news articles, whereas the search on the right pulls up specific exploits. Search better.
In addition - one thing I rarely see people ever talk about is understanding the underlying vulnerable software or component. Imagine after enumeration you discover CodeIgniter CMS. After fuzzing various parameters, you discover an error that is indicative of SQLi.
Well, Offensive Security disallows the usage of SQLmap. The best thing to do is pull up a SQLi cheat sheet and see what works right? No. Wrong.
Look at the software. Look at the components. You know it’s CodeIgniter CMS version 4.2.0 – so Google the issue to see if you can find an exploit. Be VERY specific, otherwise you might not find it.
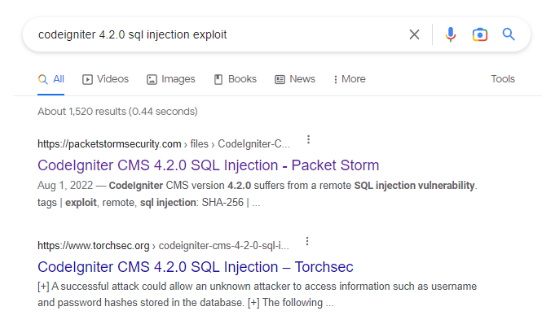
By doing this, you’ve effectively saved yourself hours of fuzzing. You can now reduce the time you spend figuring out which type of SQLi is working, and start focusing on crafting relevant queries to steal the data that will get you into the admin panel of the CMS. This is one small example of thousands of vulnerability types and combinations.
Googling will be the most effective part of your career as a hacker. You’ll want to retain and utilize public cheat sheets for various attack methods, rather than sit and hammer away aimlessly. Exploitation is a science, and when you have to rely on manual methodology, find a way to automate it.
Exploitation process
Describing the process of exploiting vulnerabilities is always the most complex part of any guide, just because there are thousands of different methods and ways to accomplish this. If you’ve utilized all the previous described resources, you should be able to find easy wins and exploits to use against systems.
Rather than talking about specific vulnerabilities, understanding what not to do is more important.
- Avoid spending more than 2 hours on any given attack vector. If you can’t get it to work after 2 hours, rotate to something different, or take a short break.
- Look at the code. For example, don’t attempt to exploit a login panel that doesn’t appear to even be passing requests to an API or backend.
- Don’t spend too much time on a vector just because it seems vulnerable. If you manage to login to an FTP server using an anonymous login flaw, does the FTP server contain anything interesting? If the FTP has no files, no capacity to upload or access files on the frontend, or isn’t a version vulnerable to FTP traversal – maybe you should look at a different vector.
- Don’t waste your metasploit. Save metasploit as a last resort, where possible. It could be the difference between immediately achieving privilege escalation versus spending hours on something stupid.
Pro tips:
- Acquiring an active directory user’s password or hash is a huge win.
- You can use crackmapexec with the -H switch to perform exploitation with a hash, even if you don’t know the password of the user.
- You can RDP into a box using xfreerdp and /pth: – GUI access into an AD machine makes exploitation crazy easy because you can use all of the native windows tools to enumerate and find weaknesses.
- If you’re NT Authority\System on the initial Active Directory system that you got a foothold on, that’s not the end of the line. You’re not going to be able to pivot until you pwn a domain user or domain admin. With this permission set, focus your efforts on dumping hashes, gathering credentials, impersonating other users, stealing tickets, etc.
- If you’re not familiar with Bloodhound, the OSCP exam is not the time to learn. You’ll waste a lot of time setting it up and also learning. If you’re going this route, learn everything about it prior, and get fast at setup.
- If you use metasploit, IMMEDIATELY run windows or linux exploit suggestor. It’s basically an autopwn.
Post-exploitation/Privilege Escalation
If you are someone who struggles with privilege escalation, I highly recommend the following
- Windows Privilege Escalation for Beginners - TCM Academy
- Linux Privilege Escalation for Beginners - TCM Academy
In addition, there are two cheat sheets that you will want to live off of. Especially if traditional methods of privilege escalation or downloading files necessary for a reverse shell aren’t possibly through ordinary means.
Other easy wins
- Linux: Capabilities, SUIDs/GUIDs, cronjobs, modifiable binaries running as root, out-of-date binaries, known-binary exploits, history files.
- Windows: Weak service permissions, Unquoted service paths, outdated binaries, scheduled tasks, custom functionality implemented through binaries, known-binary exploits, stored passwords, pass-the-hash.
Nearly all of these techniques can be found in HackTricks and within other public cheat sheets. Look around, try new methods out.
Final thoughts
If you’re struggling with specific concepts, especially web application exploits – one of the best resources for honing your skills would be PentesterLab or Web Security Academy by Portswigger. Manual web application attacks are always very difficult for new hackers. It’s recommended that you rip the band-aid off sooner rather than later and deep dive the attacks you’re weak at.
One last pro tip:
Simplify your life