Indian Government Breach, Massive Amount of Critical Vulnerabilities
Executive Summary
Sakura Samurai knew that the Indian Government operated an RVDP (Responsible Vulnerability Disclosure Program). Jackson Henry put a list together of initial assets in scope for Sakura Samurai to legally test. Robert Willis reported that he had found sensitive data and was able to breach police assets. Jackson Henry was working in the enumeration processes with his friend, Zultan Holder [not an active Sakura Samurai member] and identified a slew of various attack vectors, immediately resulting in the exposure of many pairs of credentials for databases and other pertinent applications.
The team was informed of the initial enumeration results as they continued to work on the list of assets within scope, while also further jumping into the research and began performing analysis on the sensitive data, identifying additional vectors of attack, exposed PII, and even more credentials.
Sakura Samurai team members included Jackson Henry, Robert Willis, Aubrey Cottle, and John
In total, the following vulnerabilities were identified, in no specific order:
- 35 Separate Instances of Exposed Credential Pairs (Servers, Important Applications, etc)
- 3 Instances of Sensitive File Disclosure
- 5 Exposed private-key pairs for servers
- 13K+ PII Records [and those are only the records that we were inadvertently exposed to]
- Dozens of Exposed Sensitive Police Reports
- Session Hijacking Chained via Multiple Vulnerabilities, resulting in the compromise of extremely sensitive government systems
- Remote Code Execution on a sensitive financial server; a server that contained large backups of Financial Records
Critical Findings
First and foremost, it is important to note that so many Critical findings had been identified during our testing that we cannot possibly include all of the vulnerabilities without making this writeup unnecessarily heavy. Therefore, we have opted to include small snippets of repetitive findings in this section. Many variations of application and server credentials also were obtained but the point has already been made.
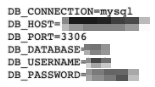
Exposed Database Credentials
Private SSH Keys

Sensitive File Exposure

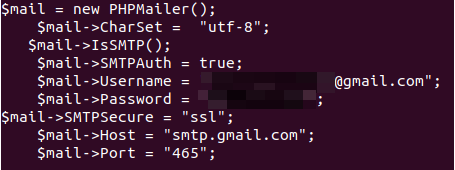
Exposed PHP Mailer Credentials
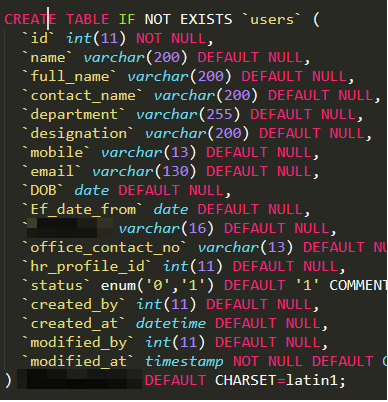
Exposed PII & Escalation
Robert Willis identified an application that resulted in a vulnerability that allowed him to access Sensitive Police Records, containing PII of individuals listed on the report. In addition, sample forensic reports and forensic tooling that is used by the police department was identified by Willis. The exposure of citizen’s sensitive information, some being victims, is a sensitive subject within itself and highly alarming.

Shortly after, Jackson Henry found a vulnerability that resulted in the exposure of 14,000+ user records. The records included a wide range of sensitive information, including full name, contact info, employee’s department, date of birth, etc. These exposed records along with other various SQL server dumps and Rob’s Police Record Exposure is enough to constitute a data breach without even logging into any of the servers.
Henry identified many credential pairs which could have resulted in even more exploitation of many other people. The PII identified is a small sample of a much larger issue.
John Jackson was able to identify a relevant Remote Code Execution Vulnerability, affecting an out-of-date application residing on one of the government servers. The remote code execution vulnerability allowed for complete access to sensitive files on the server, including the ability to exfiltrate complete backups of financial records [although data exfiltration wasn’t performed to avoid unnecessary action]

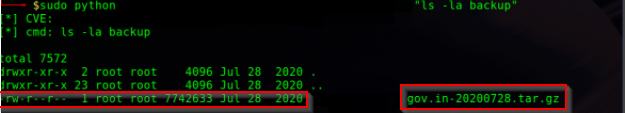
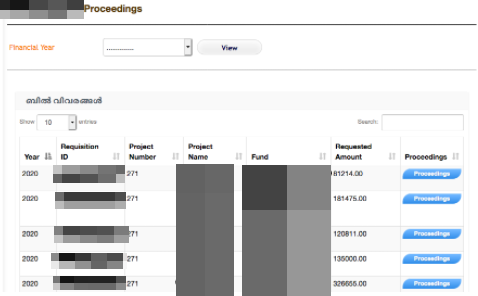
Finally, Aubrey Cottle identified the presence of what appeared to be an extremely important application being hosted by the same server that John had achieved successful Remote Code Execution on. Cottle then chained together multiple vulnerabilities in conjunction with the Remote Code Execution vulnerability, resulting in the ability to hijack any user’s session on the web application. The application contained troves of sensitive government data and could have given a threat actor the ability to perform highly-critical, admin-based government actions.
Disclosure, Communication & Remediation Complexities
Even though the Indian Government has a RVDP in place, we didn’t feel comfortable disclosing the vulnerabilities right away. The hacking process was far from the standard situation of business-as-usual security research. In total, our report compounded to a massive 34 page report worth of vulnerabilities. We knew that our intent was good, but we wanted to ensure that the US Government had eyes on the situation. Sakura Samurai coordinated with the U.S. DoD Vulnerability Disclosure Program (VDP) to assist in facilitating initial conversations of disclosure. John Jackson spoke with DC3’s Program Manager via email and coordinated on a plan of action.
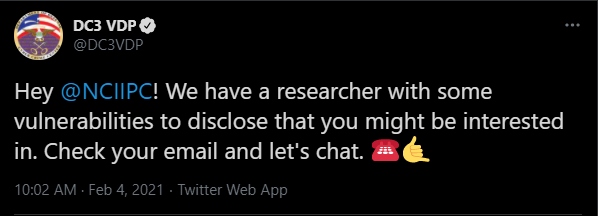
Roughly 4 days later, after further communication with the DC3, we felt safe to begin our initial reveal of research on the NCIIPC’s RVDP program.
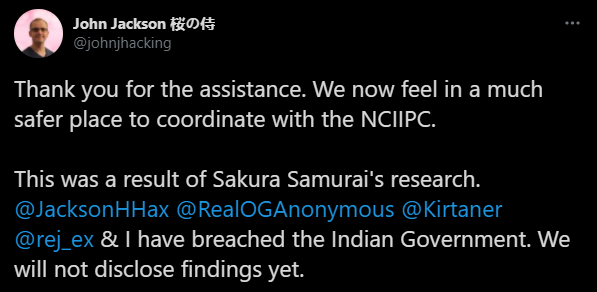
In addition, the DC3 also commended the hacking that we did in support of making the cyberspace a better place for everyone.
Unfortunately, what seemed like a done deal turned out to be quite the unprofessional ride. Any organization knows that fixing breach-worthy vulnerabilities is extremely time sensitive. Once threat actors catch wind of major vulnerabilities against an organization they begin poking on their own, looking for more vectors of attack. Immediately upon revealing that Sakura Samurai was the group responsible for hacking the Indian Government, we followed up with them via Email.
Timeline
2021/02/04 - DC3 begins initial contact with the Indian Government.
2021/02/08 - Sakura Samurai informs the public that they breached the Government.
2021/02/08 - Sakura Samurai makes contact with the NCIIPC, noting that the report that they received was a result of their research.
2021/02/09 - The NCIIPC responds, with a basic acknowledgement and thank you for the research.
2021/02/09 - Sakura Samurai asks for clarification on patching and the responsibility of breach disclosure to the public.
2021/02/10 - Sakura Samurai, having received no response, asks for an update on the involved remediation and breach notification processes.
2021/02/16 - Sakura Samurai once again asks for NCIIPC’s plans for remediation and disclosure.
2021/02/17 - The NCIIPC makes contact, 7-days later, stating that they will follow up in a short time. Again, we ask about plans of anticipated patching and breach notification to the affected citizens.
2021/02/19 - In the morning, we ask again about patching and disclosure, 8-hours later and still no response on the matter.
2021/02/19 - Sakura Samurai reviews the submitted vulnerability report and notes that only about an eighth or less of the submitted Critical Vulnerabilities have been resolved within a two-week period. No notification of breach has occurred even though Government Employees and Indian Citizens are at risk of exploitation from threat actors.
Final Notes
Governments have an obligation to protect the private data of its employees and citizens. In addition, the exposure of proprietary government data can be used for great means of manipulation and for other destructive purposes. While the NCIIPC operates a Responsible Vulnerability Disclosure Program, the recklessness and avoidance of communication represents the complete opposite of a responsible program. A failure to release notification of breach to affected citizens and to patch highly-critical vulnerabilities in a timely manner reflects poorly on the state of their Information Security posture. The clock to patch vulnerabilities began immediately when the DC3 contacted the NCIIPC via Twitter, as it is a highly visible space - one which threat actors avidly monitor.
Sakura Samurai urge the NCIIPC to patch the remainder of the vulnerabilities. The criticality of some of the issues cannot wait weeks or months for adequate resolution.
Check out our website
https://sakurasamurai.org
Twitter Links:
Main Page
https://twitter.com/SakuraSamuraii
Founders
https://twitter.com/johnjhacking
https://twitter.com/nicksahler
Members
https://twitter.com/JacksonHHax
https://twitter.com/Kirtaner
https://twitter.com/rej_ex
https://twitter.com/endingwithali
Collaborator
https://twitter.com/orpheus9001